What is Penetration Testing?
Penetration Testing is a cybersecurity practice where professionals simulate real-world cyberattacks to identify and exploit vulnerabilities in computer systems, networks, and applications. Penetration testers use a variety of techniques, including reconnaissance, vulnerability scanning, social engineering, and exploit development, to test an organization's cyber defense against potential cyber threats.
What is a Penetration Test and How Can it Help You?
A penetration test test’s the extent to which a malicious actor could exploit a vulnerability and the potential impact on an organization’s security and business. A penetration tester simulates real-world attack scenarios, mimicking the techniques of cybercriminals to determine how deep they can infiltrate a system and what sensitive data or assets they can access. By doing so, organizations gain valuable insights into their security weaknesses, enabling them to strengthen defenses before an actual attack occurs.
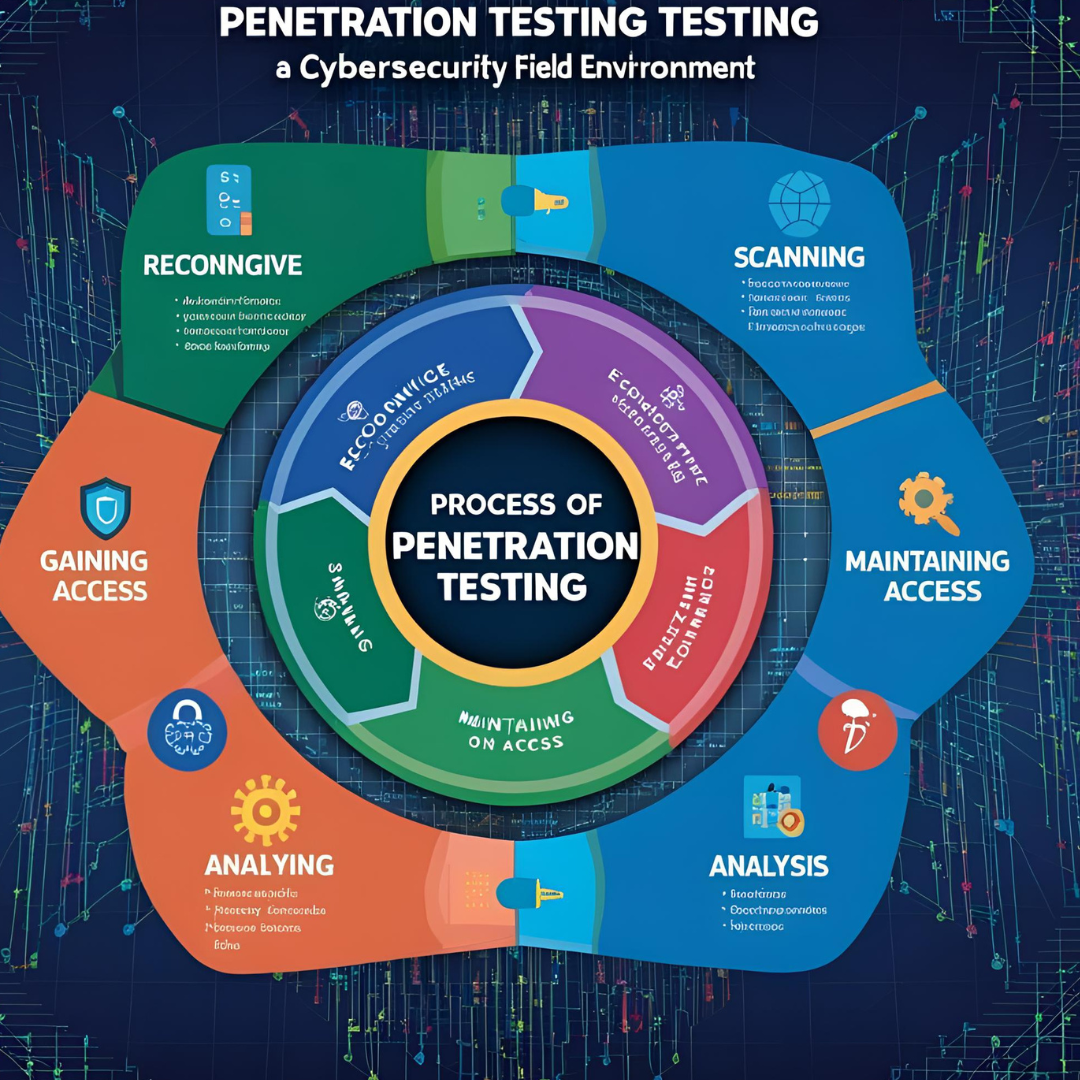
A Penetration Test Would Follow These Steps:
- Reconnaissance: The first phase involves gathering as much information as possible about the target system, including its network structure, operating systems, and applications. Attackers use this intelligence to identify potential vulnerabilities and plan their approach.
- Scanning: This phase involves actively probing the target system using tools to detect open ports, active services, and network traffic patterns. The goal is to identify weak points that could be exploited in later stages.
- Vulnerability Assessment: The collected data is analyzed to identify security weaknesses and determine their exploitability. This step helps penetration testers prioritize the most critical vulnerabilities for further testing.
- Exploitation: Testers attempt to breach the system by exploiting identified vulnerabilities, simulating real-world attacks to assess the extent of potential damage. This phase helps determine how much access an attacker could gain and what sensitive data could be compromised.
- Reporting: A report is created detailing the vulnerabilities found, the methods used to exploit them, and recommendations for remediation. This final phase provides organizations with actionable steps to strengthen their security defenses.